What Is XSS (Cross-Site Scripting)?
Cross-Site Scripting, or XSS, is a security flaw in websites that lets attackers add harmful scripts to web pages. Most of the time, these scripts are written in JavaScript.
If someone visits a page affected by XSS, their browser runs the attacker’s script. This can result in stolen cookies, hijacked sessions, or actions taken without the user’s permission.
XSS, like SQL Injection, is regularly listed in the OWASP Top 10 as one of the most common web application vulnerabilities.
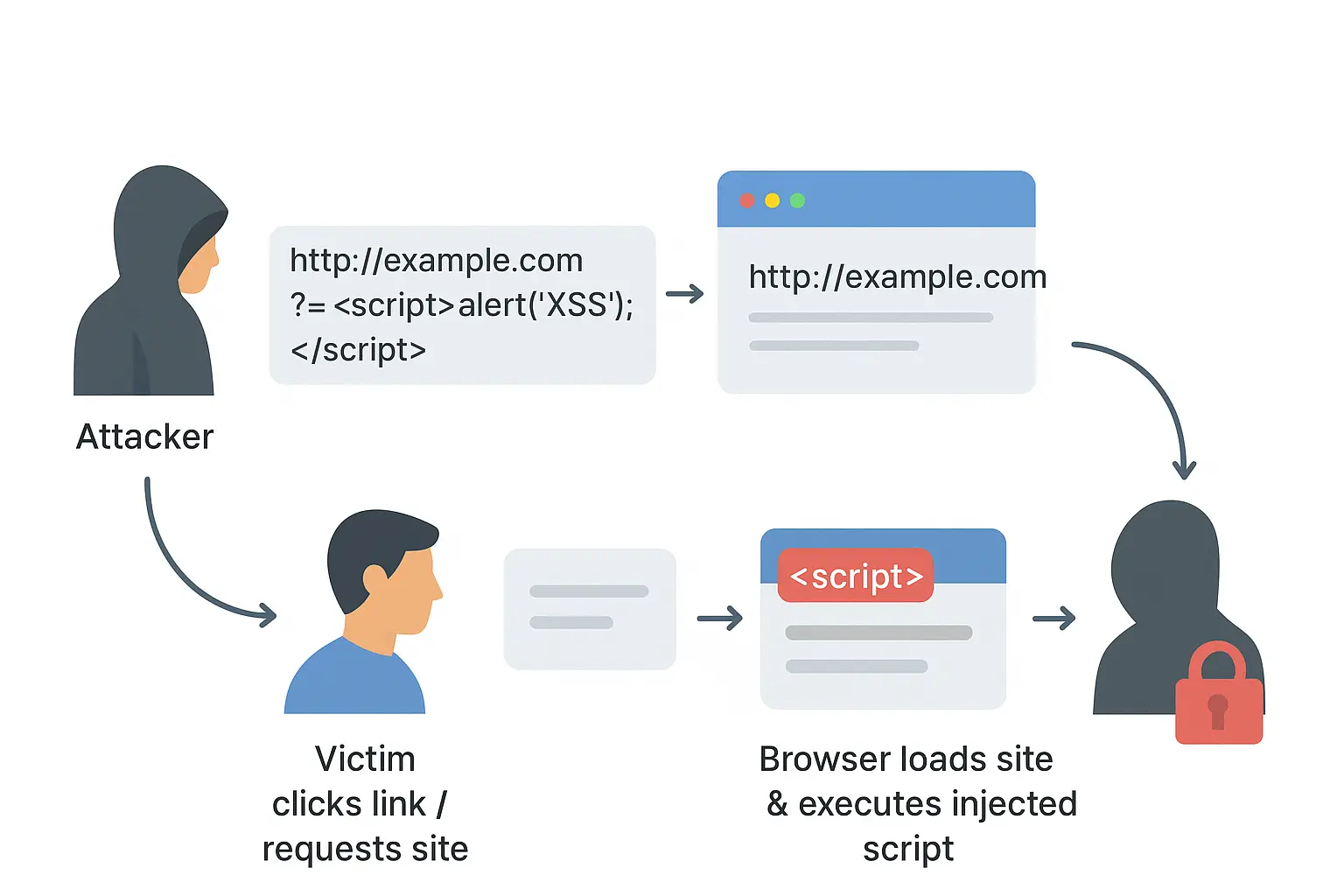
How XSS Works ?
XSS often targets web applications that do not correctly check and clean user input.
For example, if a comment box allows raw HTML or JavaScript without any filtering, an attacker could add code like this:
<script>alert('Hacked!');</script>When victims view the page, the malicious code runs inside their browser.
Why XSS Matters in Cybersecurity
XSS can lead to a bigger breach :
- Account takeover (stealing session cookies to impersonate users)
- Data theft (capturing form inputs like passwords or credit cards)
- Phishing attacks (injecting fake login forms)
- Malware delivery (redirecting users to malicious websites)
Types of XSS
- DOM-Based XSS
- The attack happens entirely in the browser by manipulating the Document Object Model (DOM) without involving the server.
- Stored XSS
- Malicious script is permanently stored on the server, such as the database, profile page.
- Reflected XSS
- Script is reflected off a web server (e.g, in URL or error message), the script will be executed when the victim clicks crafted link by attackers.
How to Prevent XSS
- Input sanitization & output encoding : always cleaning user input data before processing it, transforming user input into a safe format
- Use Content Security Policy (CSP) : restricts what script can be executed in the browser.
- Avoid eval() and inline JavaScript : to reduce injection risks.
- Security testing (DAST/IAST) : run security testing to detect vulnerabilities early
Example in Real World Case - Samy worm (MySpace, 2005)
What happened: Samy Kamkar published a MySpace profile that contained a stored XSS payload. When other users viewed the profile, the payload ran in their browsers, it (a) added Samy as a friend, (b) appended the phrase “Samy is my hero” to their profiles, and (c) replicated itself to those users’ profile pages.
Impact: The worm self-propagated to ~1 million users within ~20 hours, forcing MySpace offline temporarily.
Why it worked: MySpace allowed unescaped HTML/attributes in profile fields, enabling stored script execution in visitors’ browsers.
Lessons / fix: Proper output encoding, input sanitization, removal of HTML in profile fields, and rapid patching. Samy later faced legal consequences, and MySpace deployed filters.
Related Terms
- SQL Injection
- DAST (Dynamic Application Security Testing)
- OWASP Top 10
- CSRF (Cross-Site Request Forgery)